Access Control Explained
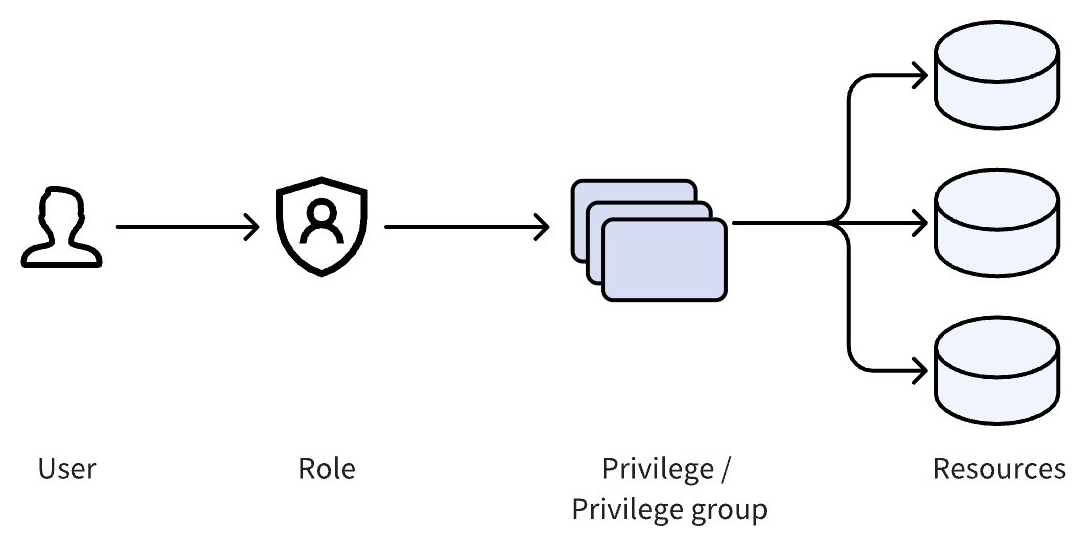
Zilliz Cloud implements Role-Based Access Control (RBAC) to finely control access to resources in Zilliz Cloud. RBAC (Role-Based Access Control) is a security measure that grants privileges to roles rather than directly to users. These roles, which contains specific privileges to resources, are then granted to users, enabling efficient management of user access control.
Zilliz Cloud RBAC architecture
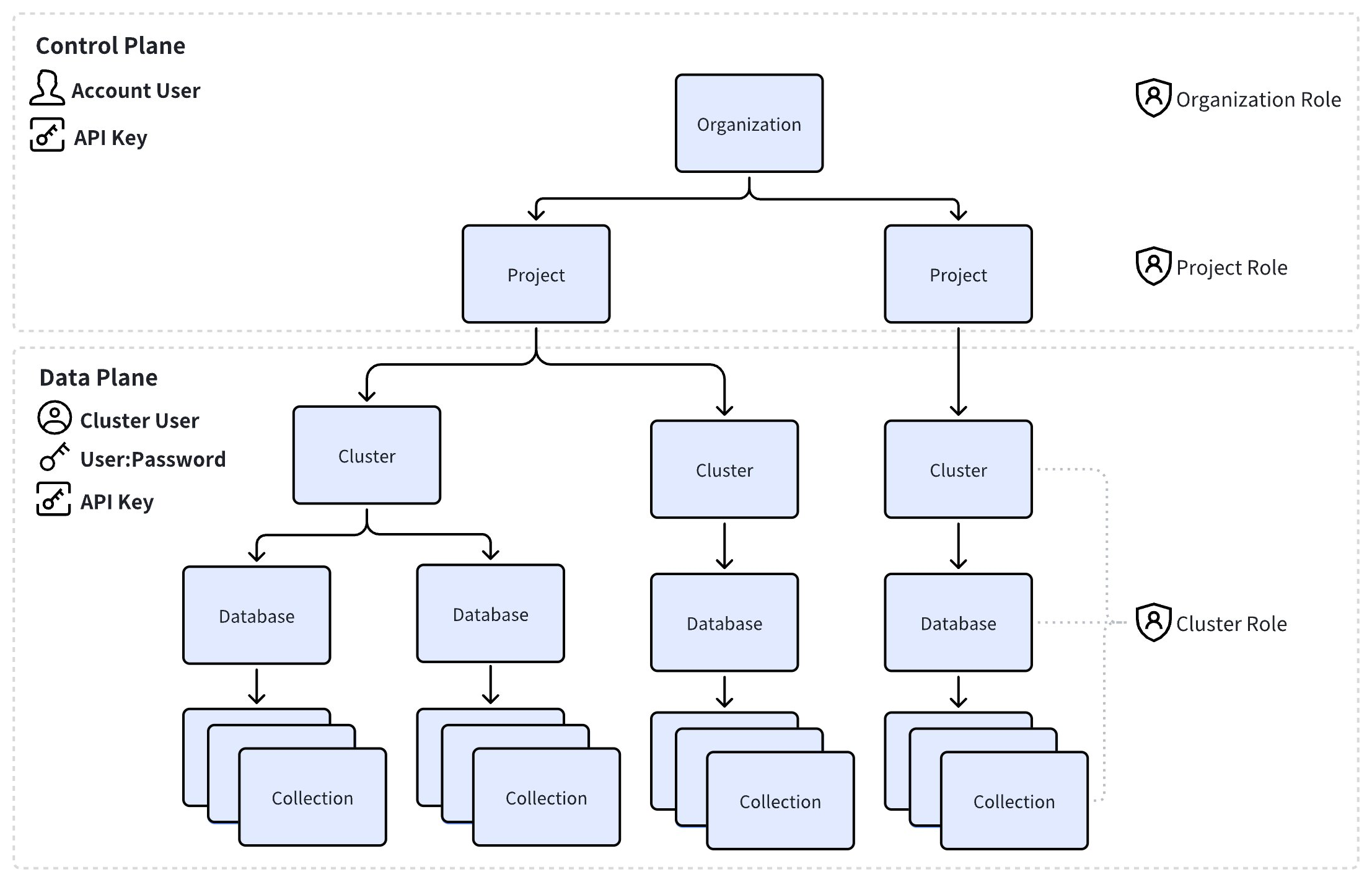
Zilliz Cloud organizes its resources within two planes, implementing RBAC across both:
-
Control plane: This plane encompasses organizations, projects, and cluster management. Account users are granted specific organization and project roles and authenticate via API keys when interacting with resources on the control plane.
-
Data plane: This plane includes clusters, databases, and collections, focusing on data access management. Cluster users are granted appropriate cluster roles and authenticate using API keys or username-password pairs when interacting with data plane resources.
Normally, each account user corresponds to a cluster user. However, not all users require access for both planes. In some cases, a control plane account user like a Billing Admin might only need access to the control plane for billing management purposes and do not require data plane access. Conversely, temporary cluster users can be created and granted access to data plane resources through customized API keys, allowing data access without a registered account. For details about managing customized API keys, refer to API Keys.
Roles and privileges
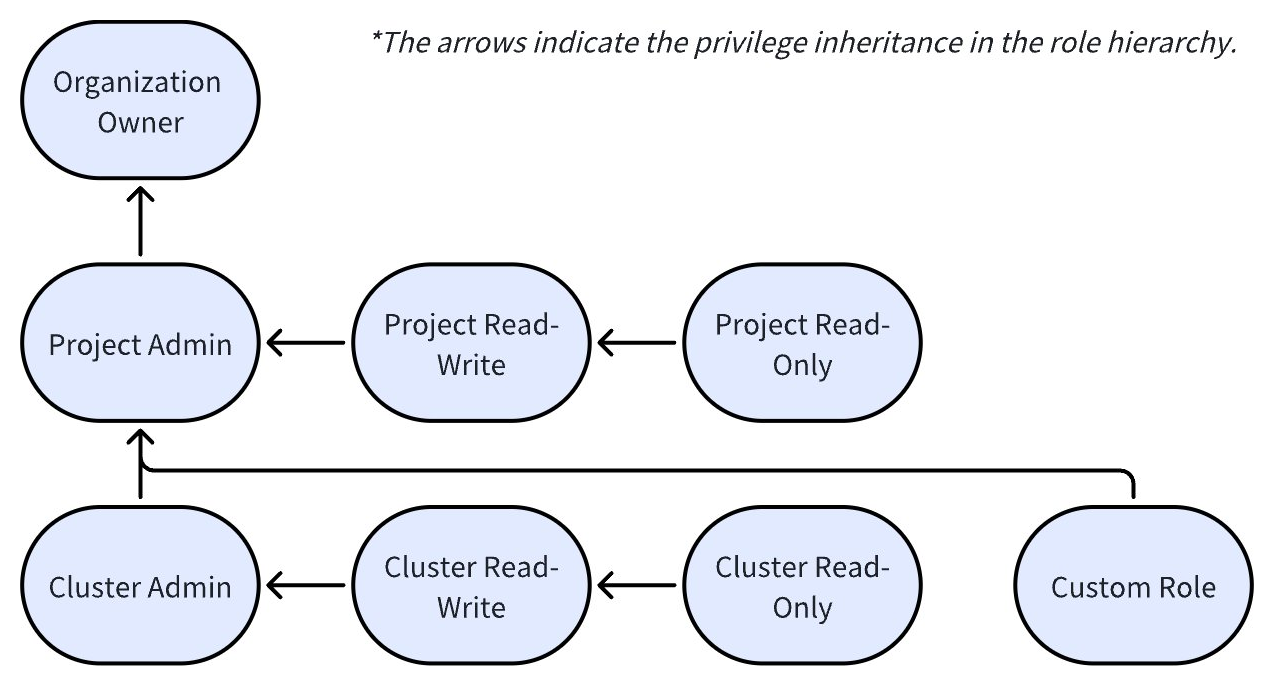
Account users are granted organization roles and project roles while cluster users are granted cluster roles that control access to cluster, databases, and collections. The following diagram illustrates the hierarchy for roles in Zilliz Cloud.
-
On the organization level
- The Organization Owner role encompasses comprehensive privileges across all projects and clusters.
For details about all organization roles, refer to Organization roles.
-
On the project level
-
The Project Admin role includes all privileges of a specific project and privileges across all cluster.
-
The Project Read-Write role has the privileges to view a project and manage its resources.
-
The Project Read-Only role has the privileges to view a project and its resources.
For details about project roles, refer to Project roles.
-
-
On the cluster level
-
The Cluster Admin role includes all privileges of a specific cluster.
-
The Cluster Read-Write role has the privileges to view a cluster and manage all its resources.
-
The Cluster Read-Only role has the privileges to view a cluster and its resources.
-
Additionally, custom roles can be created at this level to precisely manage privileges to cluster resources, such as databases and collections.
For details about cluster roles, refer to Manage Cluster Roles (Console).
-
Implement RBAC in Zilliz Cloud
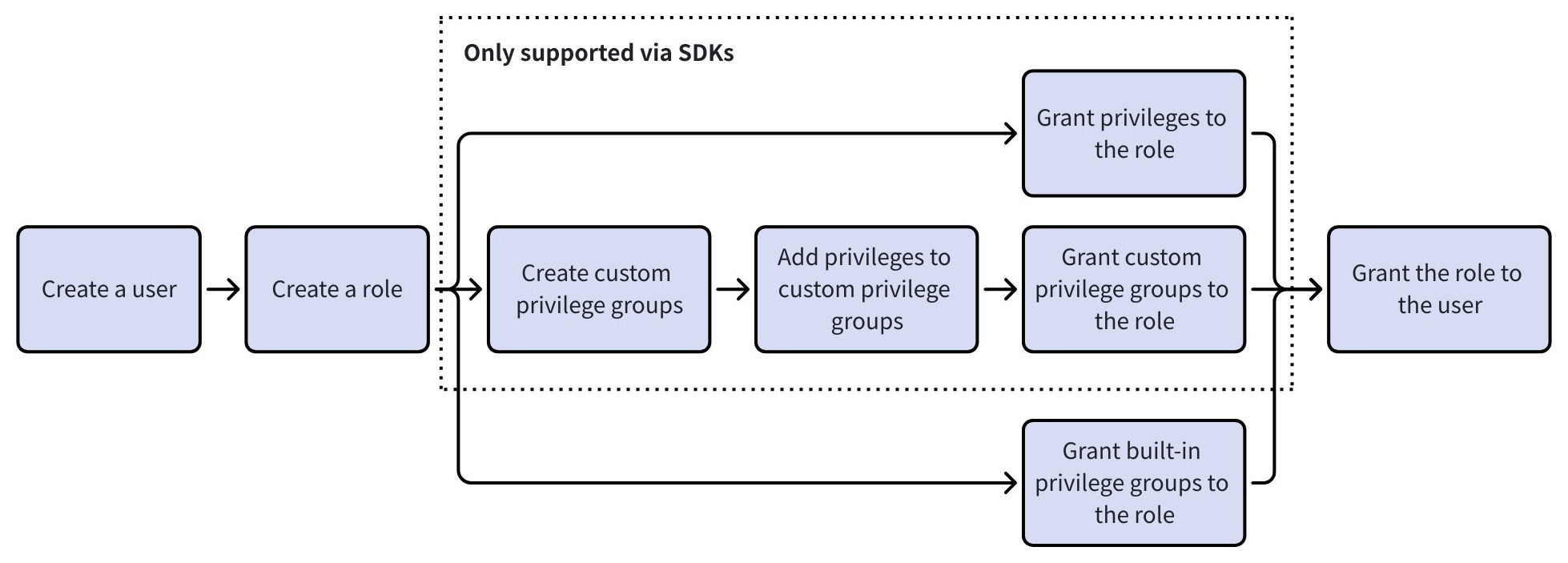
The following diagram shows the complete workflow to implement RBAC in Zilliz Cloud.
-
Create a user: In addition to the default user
db_adminin Zilliz Cloud, you can create new users and set passwords to protect data security via the web console or using SDKs. -
Create a role: You can create customized roles via the web console or using SDKs. The specific capabilities of a role are determined by its privileges.
-
(Optional) Create a privilege group and add privileges to the privilege group: Combine multiple privileges into one privilege group to streamline the process of granting privileges to a role. In addition to the built-in privilege groups provided by Zilliz Cloud, you can also create your own customized privilege groups using the SDKs.
-
Grant privileges or privilege groups to a role: Define the capabilities of a role be granting privileges or privilege groups to this role. Currently you can only grant built-in privilege groups to a role on the web console. To grant specific privileges or customized privilege groups to a role, please create a support ticket and then use the SDKs instead.
-
Grant roles to users: Grant roles with certain privileges to users so that users can have the privileges of a role. A single role can be granted to multiple users. You can complete this step either via the web console or using SDKs.