VectorDB Audit Logs
Audit logging allows administrators to track and monitor user-driven operations and API calls on Zilliz Cloud clusters. This feature provides a detailed record of vector db activities, including vector searches, query execution, index management, and other data operations.
Audit logging is available only for Dedicated clusters in Enterprise projects or higher plan tiers.
Audit logging is supported only for Zilliz Cloud clusters running Milvus 2.5.x.
Audit logging can be forwarded to AWS S3, Azure Blob Storage, or Google Cloud Storage.
Enabling audit logging incur charges. For details, see Audit Log.
Overview
Audit logging tracks a wide range of operations on the data plane, including:
-
Search and Query Operations: Vector searches, hybrid searches, and query operations.
-
Data Management: Index creation, collection creation, partition management, and entity operations like insert, delete, and upsert.
-
System Events: User access attempts, authorization checks, and other predefined actions.
Cluster-level data jobs such as migration, backup, and restore do not generate audit logs. To view these activity records, refer to View Activities.
Audit logs are forwarded directly to a user-designated object storage bucket at regular intervals. Logs are stored in a structured file path and naming format for easy access and management:
-
File Path:
/<Cluster ID>/<Log type>/<Date> -
File Naming Convention:
<File name><File name suffix>in the format HH:MM:SS-$UUID, where HH:MM:SS represents the time in UTC and $UUID is a unique random string. Example:09:16:53-jz5l7D8Q.
Below are examples of audit log entries forwarded to a bucket:
-
Create Collection
{
"action": "CreateCollection",
"cluster_id": "in01-0045a626277eafb",
"connection_uid": 456912553983082500,
"database": "default",
"interface": "Grpc",
"log_type": "AUDIT",
"params": {
"collection": "test_audit",
"consistency_level": 2
},
"status": "Receive",
"timestamp": 1742983070463,
"trace_id": "216a8129c06fd3d93a47bd69fa0a65ad",
"user": "key-hwjsxhwppegkatwjaivsgf"
} -
Create Index
{
"action": "CreateIndex",
"cluster_id": "in01-0045a626277eafb",
"connection_uid": 456912553983082500,
"database": "default",
"interface": "Grpc",
"log_type": "AUDIT",
"params": {
"collection": "test_audit"
},
"status": "Receive",
"timestamp": 1742983070645,
"trace_id": "4402e7bfc498dd06be1408c7e6a7954d",
"user": "key-hwjsxhwppegkatwjaivsgf"
} -
Drop Index
{
"action": "DropIndex",
"cluster_id": "in01-0045a626277eafb",
"connection_uid": 456912553983082500,
"database": "default",
"interface": "Grpc",
"log_type": "AUDIT",
"params": {
"collection": "test_audit"
},
"status": "Receive",
"timestamp": 1742983073378,
"trace_id": "066ec33c3f55d3edbf7d01c6270024e2",
"user": "key-hwjsxhwppegkatwjaivsgf"
}
Refer to the Audit Log Reference for a detailed list of supported actions and corresponding log fields.
Enable audit log
Audit logging on Zilliz Cloud forwards audit logs directly to your storage bucket.
Before you start
- You have Organization Owner or Project Admin access to the project. If you do not have the necessary permissions, contact your Zilliz Cloud administrator.
Procedure
Log in to the Zilliz Cloud console.
In the left-side navigation pane, choose Clusters.
Go to the details page of the target cluster and choose the Auditing tab. This tab will be unavailable when your cluster is in CREATING, DELETING or DELETED status.
Click Enable Audit Log.
In the Enable Audit Logs dialog box, specify your object storage integration settings.
-
Storage Integration: Select your bucket to store the audit logs.
📘NotesOnly the buckets in the same region as your cluster will appear in the drop-down list.
-
Forward Directory: Specify a directory within the bucket to store audit logs.
Click Enable. Once the Audit Log status is Active, it has been enabled successfully. If the status is Abnormal, go to FAQ for troubleshooting.
Once configured, audit logs will be forwarded to your bucket at an interval of about 5 minutes. You can access your bucket to view or manage the logs as needed.
Once your audit logs are forwarded to your S3 bucket, you can integrate your S3 storage to visualization platforms for enhanced monitoring and analysis. For instance, if you want to use Snowflake to gain deeper insights, refer to Automating Snowpipe for Amazon S3.
To understand parameters in log entries, refer to Audit Logs.
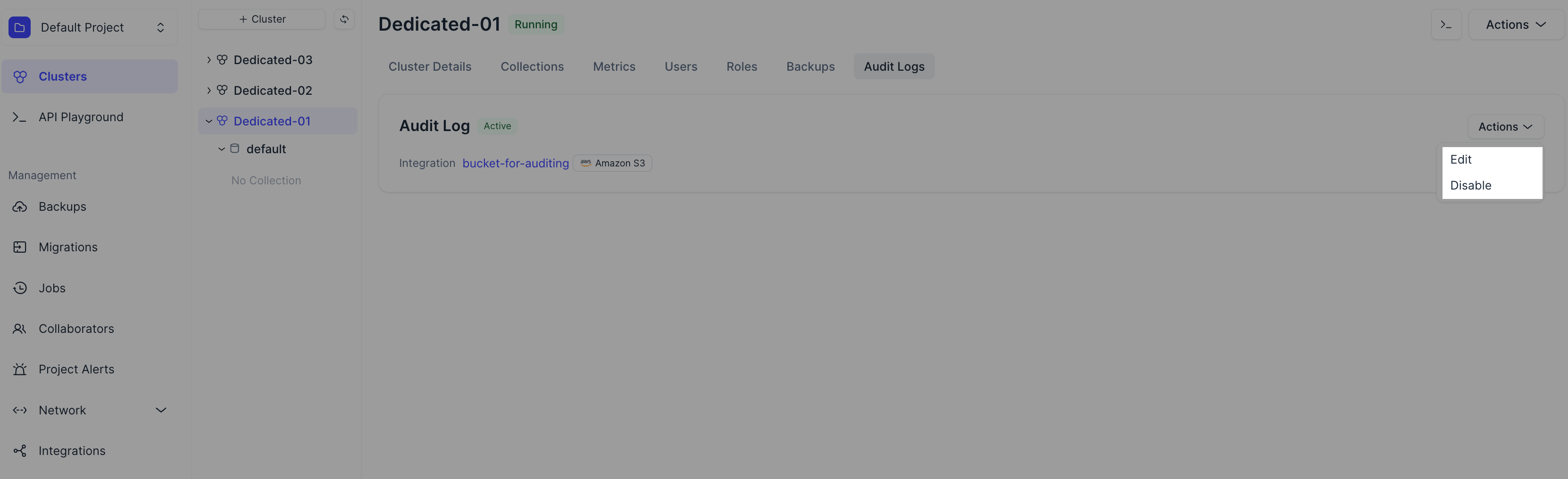
Manage audit logs
Once audit log is enabled, you can edit its configuration or disable it as needed.
FAQ
This FAQ addresses common issues and questions related to audit logging on Zilliz Cloud. For further assistance, contact Zilliz Cloud support.
-
What should I do if my Audit Log status is Abnormal?
An Abnormal status means Audit Log is experiencing an issue. Follow these steps to troubleshoot:
-
Verify your bucket: Confirm that the configured storage bucket is set up correctly and that you have the necessary permissions.
-
Contact support: If the issue persists, contact Zilliz Cloud support for further assistance.
-
-
Will an Abnormal cluster status affect the Audit Log service?
An abnormal cluster status indicates that the cluster may be experiencing issues, such as network connectivity problems or disruptions in Zilliz Cloud services. However, these issues do not impact the Audit Log service, which continues to function normally and forward logs as expected. If you encounter persistent problems, contact Zilliz Cloud support.