Deploy BYOC-I on AWS
This page explains how to deploy a Bring-Your-Own-Cloud (BYOC) data plane with a BYOC agent in your AWS Virtual Private Cloud (VPC).
Zilliz BYOC is currently available in General Availability. For access and implementation details, please contact Zilliz Cloud support.
This guide demonstrates how to create the necessary resources on the AWS console step-by-step. If you prefer to use a Terraform script to provision the infrastructure, see Terraform Provider.
Prerequisites
Ensure that
-
You are the owner of a BYOC-I organization.
-
You have been granted the permissions listed in Required permissions.
Procedures
Step 1: Prepare the deployment environment
A deployment environment is a local machine, a virtual machine (VM), or a CI/CD pipeline configured to run the Terraform configuration files and deploy the data plane of your BYOC-I project. In this step, you need to
-
Configure AWS credentials (AWS profile or access key).
For details on how to configure AWS credentials, refer to this document.
-
Install the latest Terraform binary.
For details on how to install Terraform, refer to this document.
Step 2: Create a project
Within your BYOC-I organization, click the Create Project and Deploy Data Plane button to start the deployment.
Step 3: Set up the general settings
In General Settings, you need to set the project name and determine the cloud providers and regions where Zilliz Cloud deploys the data plane for the project.
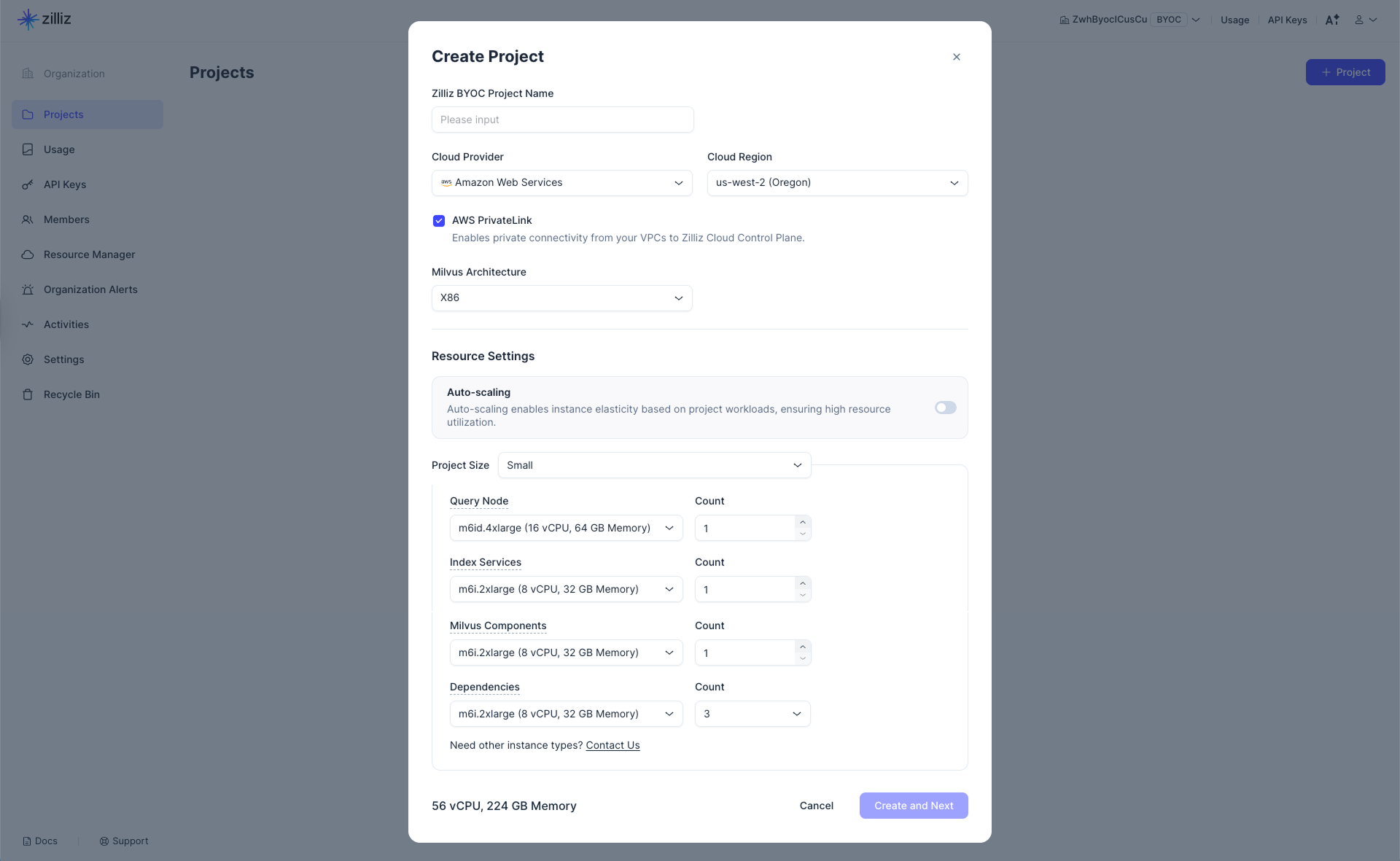
Set Project Name.
Select Cloud Provider and Region.
Determine whether to enable AWS PrivateLink.
This option allows private connectivity to the clusters within the current project. If you enable this option, you must create a VPC Endpoint for private connectivity.
Select an architecture type that matches your application in Architecture.
This determines the architecture type of the Zilliz BYOC image to use. Available options are X86 and ARM.
In Resource Settings, you need to
-
Enable or disable Auto-scaling to allow Zilliz Cloud to automatically adjust the number of EC2 instances within a defined range based on your project workloads, ensuring efficient resource use.
-
Configure Initial Project Size.
In a BYOC project, the query node, index services, Milvus components, and dependencies use different types of EC2 instances. You can set instance types and counts for these services and components individually.
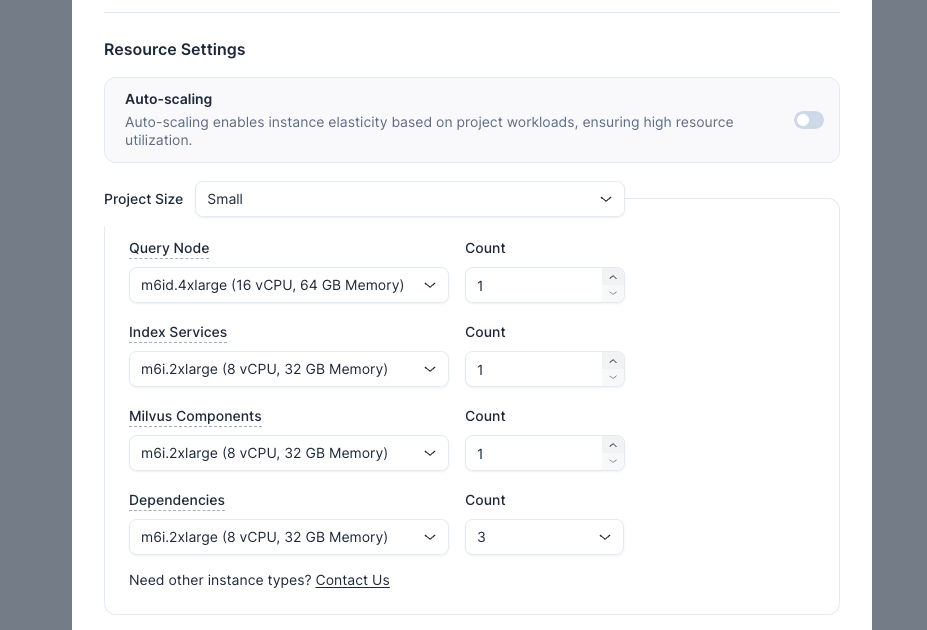
If Auto-scaling is disabled, simply specify the number of EC2 instances required for each project component in the corresponding Count field.
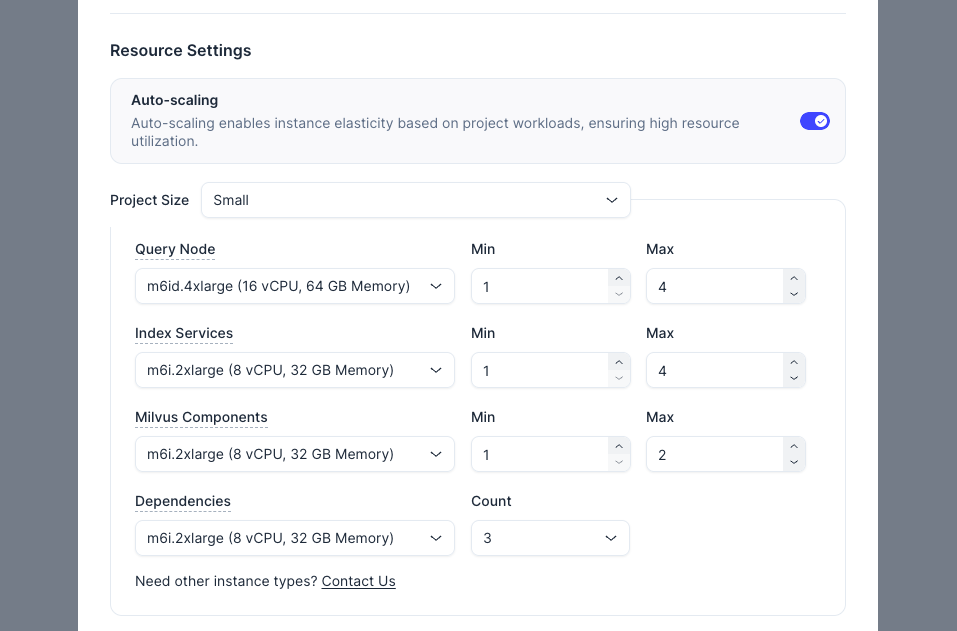
Once Auto-scaling is enabled, you need to specify a range for Zilliz Cloud to automatically scale the number of EC2 instances based on actual project workloads by setting the corresponding Min and Max fields.
To facilitate resource settings, there are four predefined project size options. The following table shows the mapping between these project size options and the number of clusters that can be created in the project, as well as the number of entities these clusters can contain.
Size
Maximum Cluster Quantity
Maximum Number of Entities (Million)
Performance-optimized CU
Capacity-optimized CU
Small
3 clusters with 8 to 16 CUs
10 Million - 25 Million
40 Million - 80 Million
Medium
7 clusters with 16 to 64 CUs
25 Million - 100 Million
80 Million - 350 Million
Large
12 clusters with 64 to 192 CUs
100 Million - 300 Million
350 Million - 1 Billion
X-Large
17 clusters with 192 to 576 CUs
300 Million - 900 Million
1 Billion - 3 Billion
You can also customize the settings by selecting Custom in Initial Project Size and adjusting the EC2 instance types and counts for all data plane components. If your preferred EC2 instance types are not listed, please contact Zilliz support for further assistance.
Click Next.
Step 4: Deploy the data plane
Follow the steps displayed in the dialog to deploy the data plane for the currently created project.
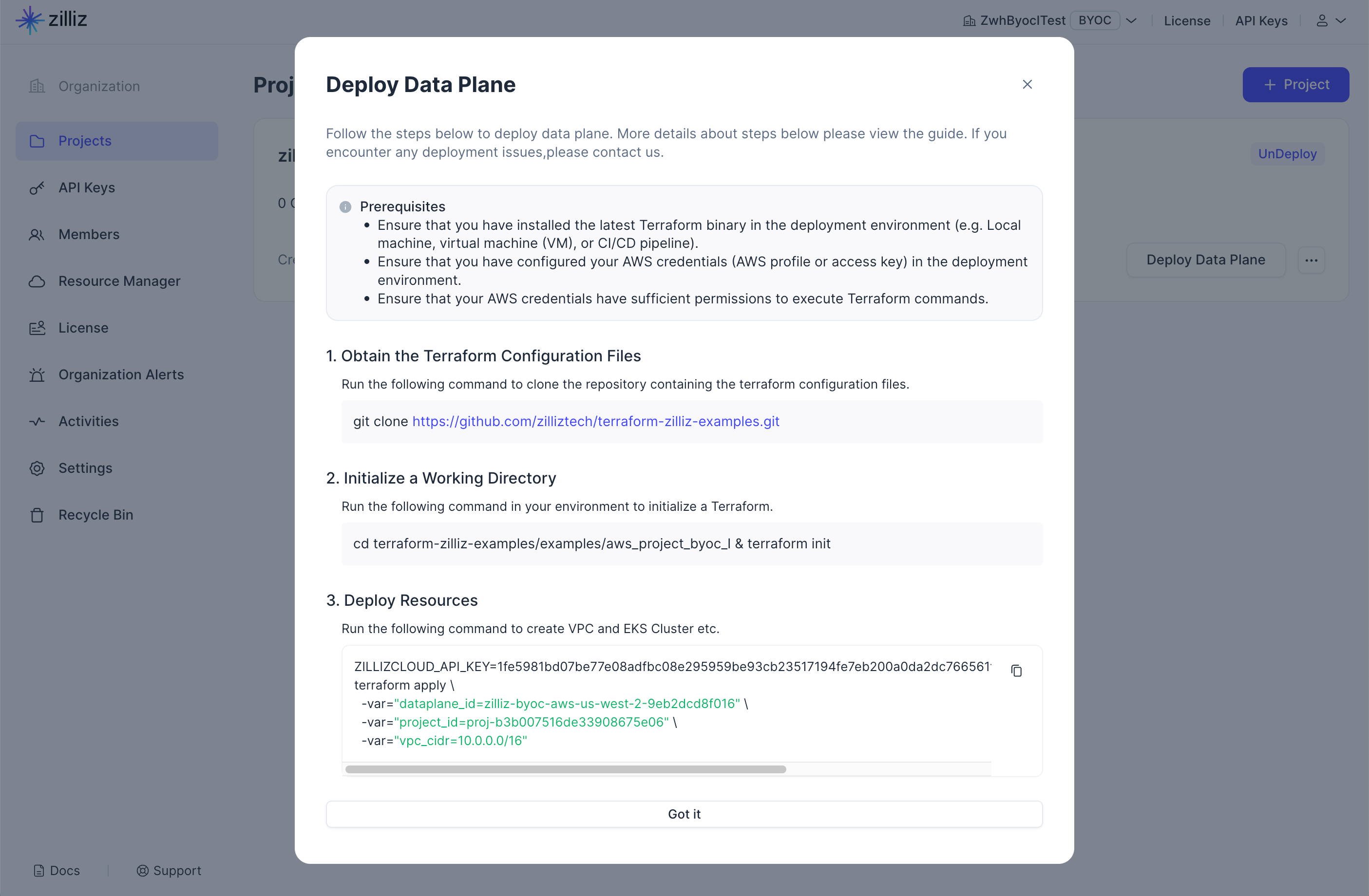
For details on running the above Terraform scripts, refer to the Zilliz Cloud BYOC-I Project Setup Guide.
Manage projects
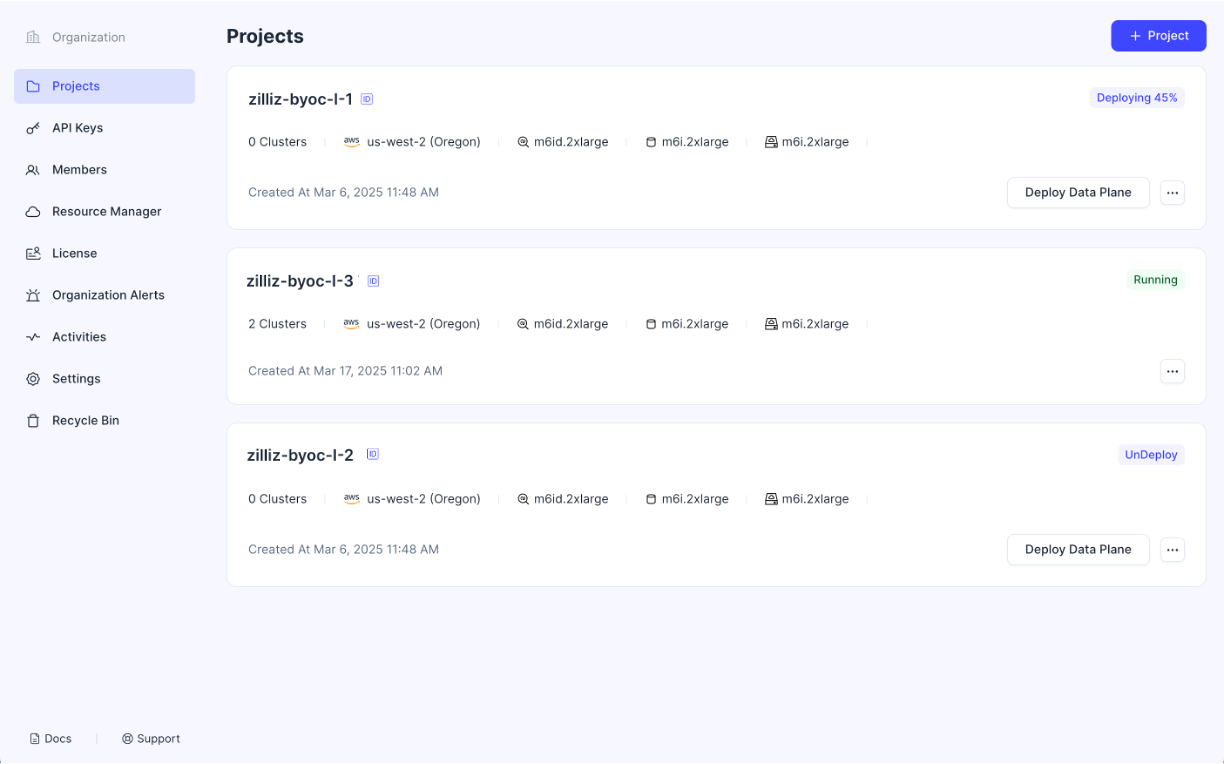
Projects with an Undeploy tag
If the status tag on the right corner of a project card reads Undeploy, you can always click the Deploy Data Plane button on the project card to reopen it. To rename or delete the project, click the ... button in the project card and select Rename or Delete from the drop-down menu.
Projects with a Deploying tag
Once you have prepared the deployment environment and executed the displayed commands, you must wait for the BYOC agent to activate. When the status tag on the project card reads Deploying and shows the progress percentage, you cannot rename or delete the project until the data plane is in place.
Projects with a Running tag
Once the status tag on a project card reads Running, you can start creating clusters in the project. To rename or delete a running project, ensure that there are no clusters in the project.
Technical support access
To assist you with troubleshooting and maintenance operations, Zilliz Cloud enables technical support to access your project's data plane by default.
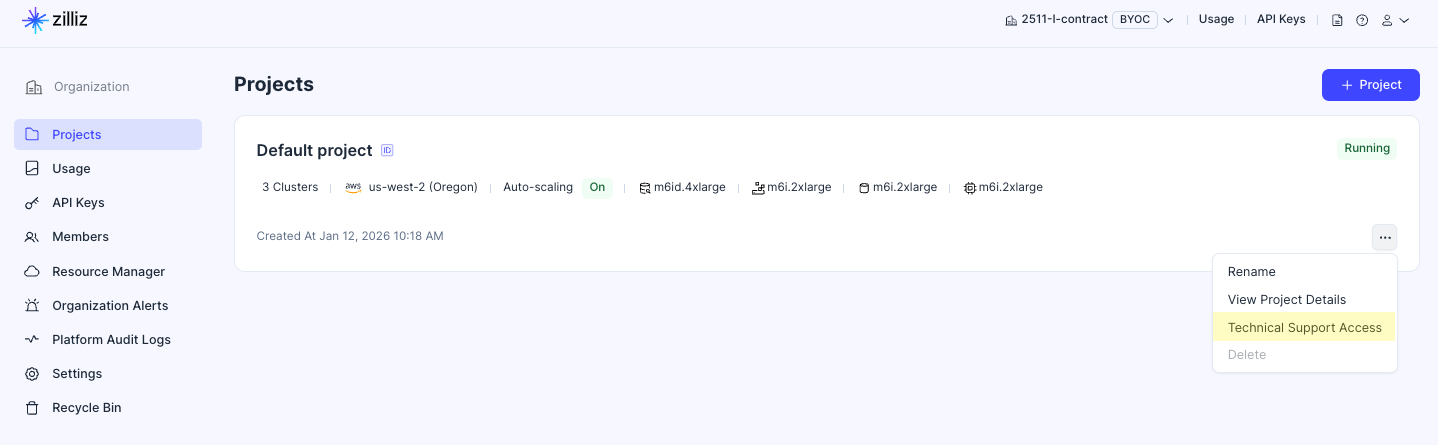
When you click Technical Support Access from the target project's drop-down menu to view the current settings.
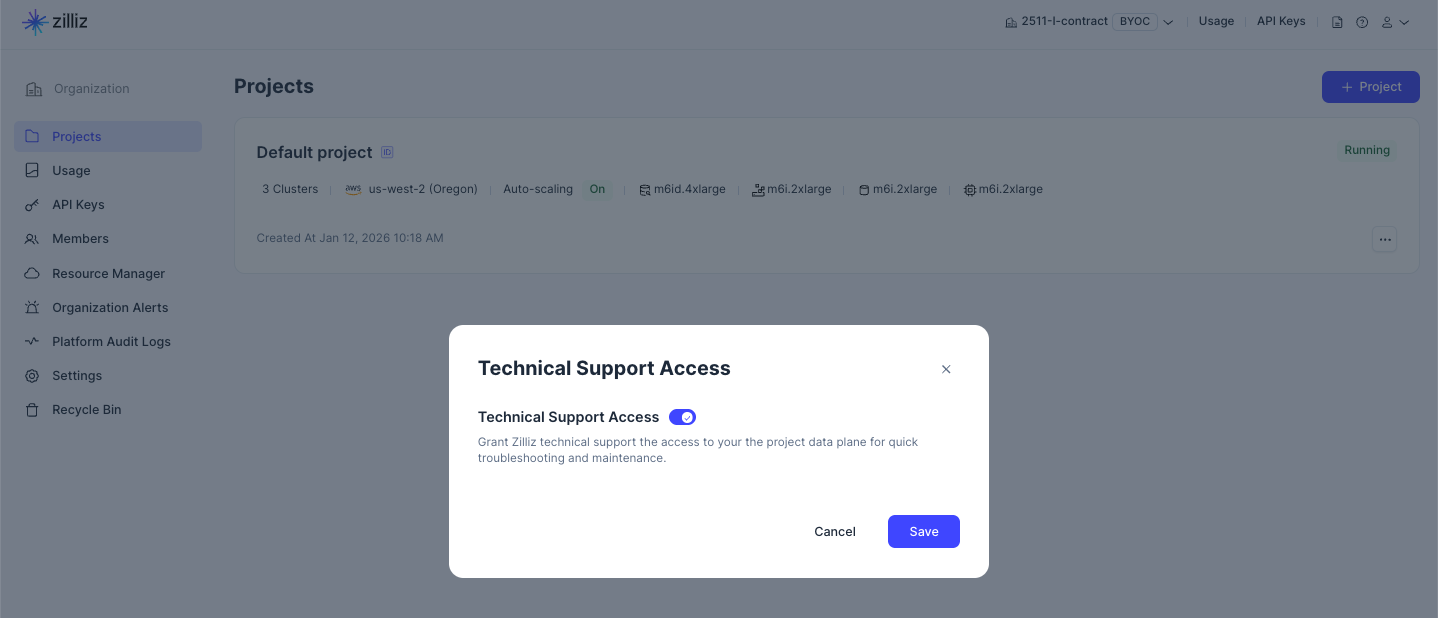
You can disable it to meet data governance and security requirements.
Required permissions
In this section, you will find all the key permissions required to deploy BYOC-I on AWS.
VPC and networking resource permissions
-
VPC Management: Create, modify, describe, and delete VPCs
-
Subnet Operations: Create and delete subnets
-
Security Groups: Create, modify, and delete security groups and their rules
-
Route Tables: Create, associate, and manage route tables
-
Internet Gateways: Create, attach, and detach internet gateways
-
NAT Gateways: Create and delete NAT gateways with Elastic IPs
-
VPC Endpoints: Create and delete VPC endpoints for AWS services
-
Launch Templates: Create and delete EC2 launch templates
-
Route53: Associate VPCs with hosted zones
-
Tagging: Create and delete tags on VPC resources
IAM roles and BYOC-I deployment permissions
-
Role Management: Create, get, list, attach/detach policies, and delete IAM roles
-
Policy Management: Create, get, list versions, and delete IAM policies
-
Tagging: Tag and untag roles and policies
-
Identity Verification: Get caller identity (STS)
S3 bucket permissions
-
Bucket Operations: Create, list, get configuration, and delete S3 buckets
-
Bucket Configuration: Manage bucket tagging, policies, ACLs, CORS, versioning, encryption, and public access settings
-
Object Tagging: Put, get, and delete object tags
-
Bucket Listing: List all buckets in the account
EKS cluster and related resource permissions
-
Service-Linked Roles: Create EKS service-linked roles for cluster and node group management
-
OIDC Provider: Create, tag, get, and delete OpenID Connect providers (with
Vendor=zilliz-byoctag requirement) -
IAM Role Management: Read EKS roles and pass roles to EKS service
-
EC2 Resources: Create launch templates, run instances, and manage tags (with
Vendor=zilliz-byoctag requirement) -
EKS Cluster Operations: Create, update, describe, tag, and delete EKS clusters
-
Node Group Operations: Create, update, describe, and delete EKS node groups
-
Addon Management: Create, update, describe, and delete EKS addons
-
Access Entry Management: Create, update, describe, and delete EKS access entries and pod identity associations