Set up a PrivateLink (AWS)
This guide demonstrates the procedure for setting up a private link from a Zilliz Cloud cluster to your service hosted in different AWS VPCs.
This feature is available only to Dedicated clusters.
A private link is set up at the project level and is effective for all clusters deployed within the same cloud provider and region under this project.
Zilliz Cloud does not charge you for creating and using private endpoints. However, your cloud provider may charge you for each endpoint that you create to access Zilliz Cloud.
Before you start
Ensure that:
- If your service and Zilliz Cloud cluster are in different regions and the service needs to access the cluster through AWS PrivateLink, submit a ticket, and we will handle your request.
Create private endpoint
Zilliz Cloud offers you an intuitive web console to add a private endpoint. Navigate to your target project and click Network > Private Endpoint in the left navigation. Click + Private Endpoint.
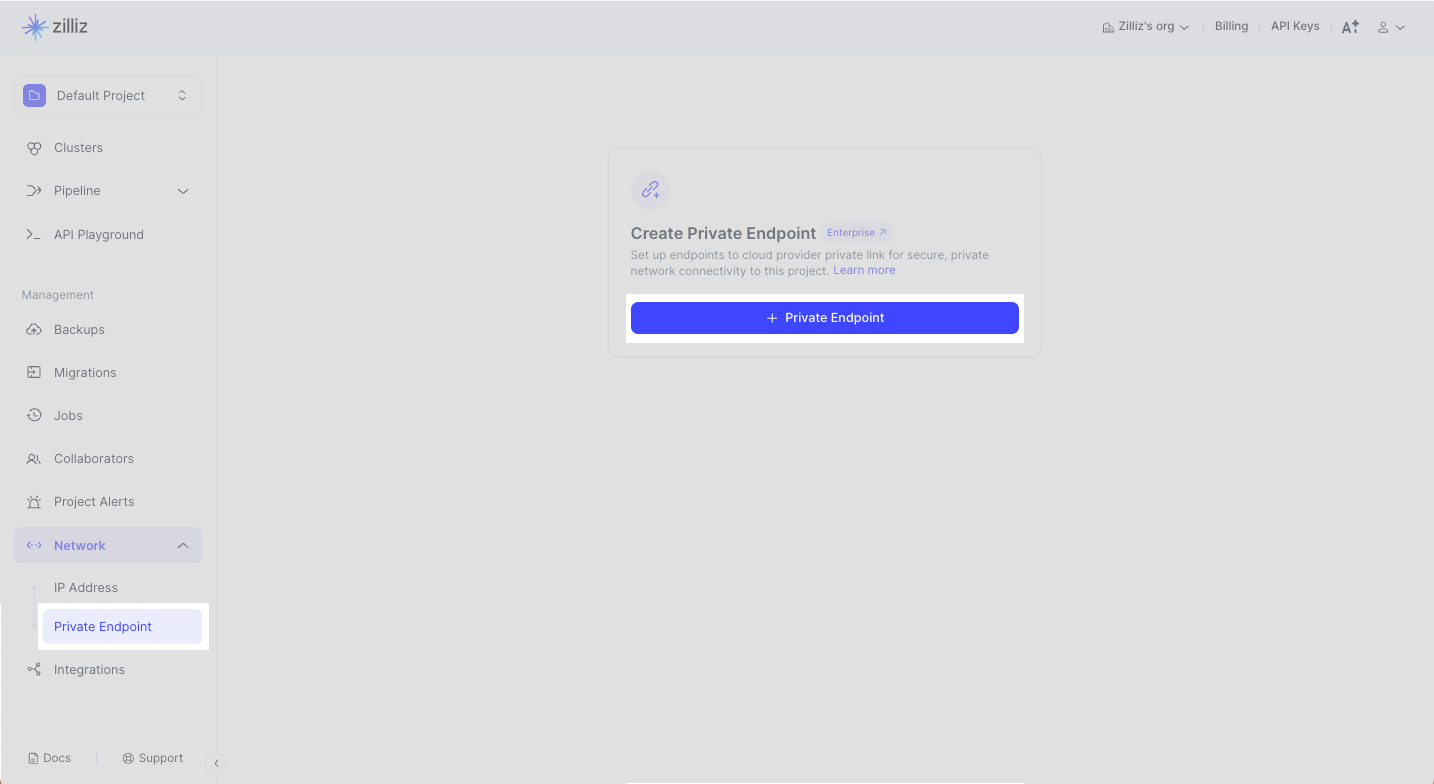
Step 1: Select a cloud provider and region
To create a private endpoint for a cluster deployed in an AWS region, select AWS from the Cloud Provider drop-down list. In Region, select the region that accommodates the cluster you want to access privately. Click Next.
For more information on available cloud providers and regions, see Cloud Providers & Regions.
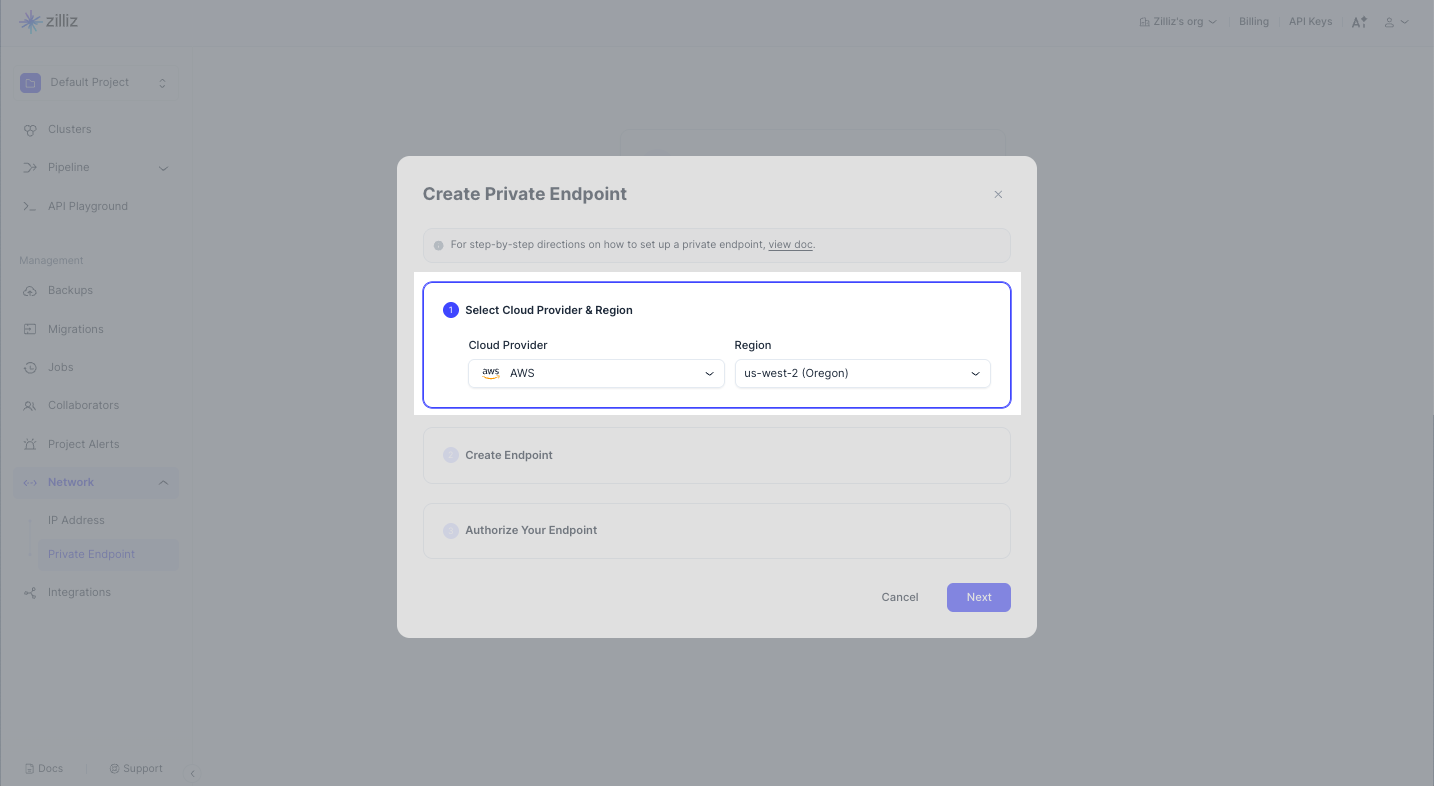
Step 2: Create an Endpoint
You need to complete this step on your cloud provider console using either the UI console or CLI.
-
Via UI console
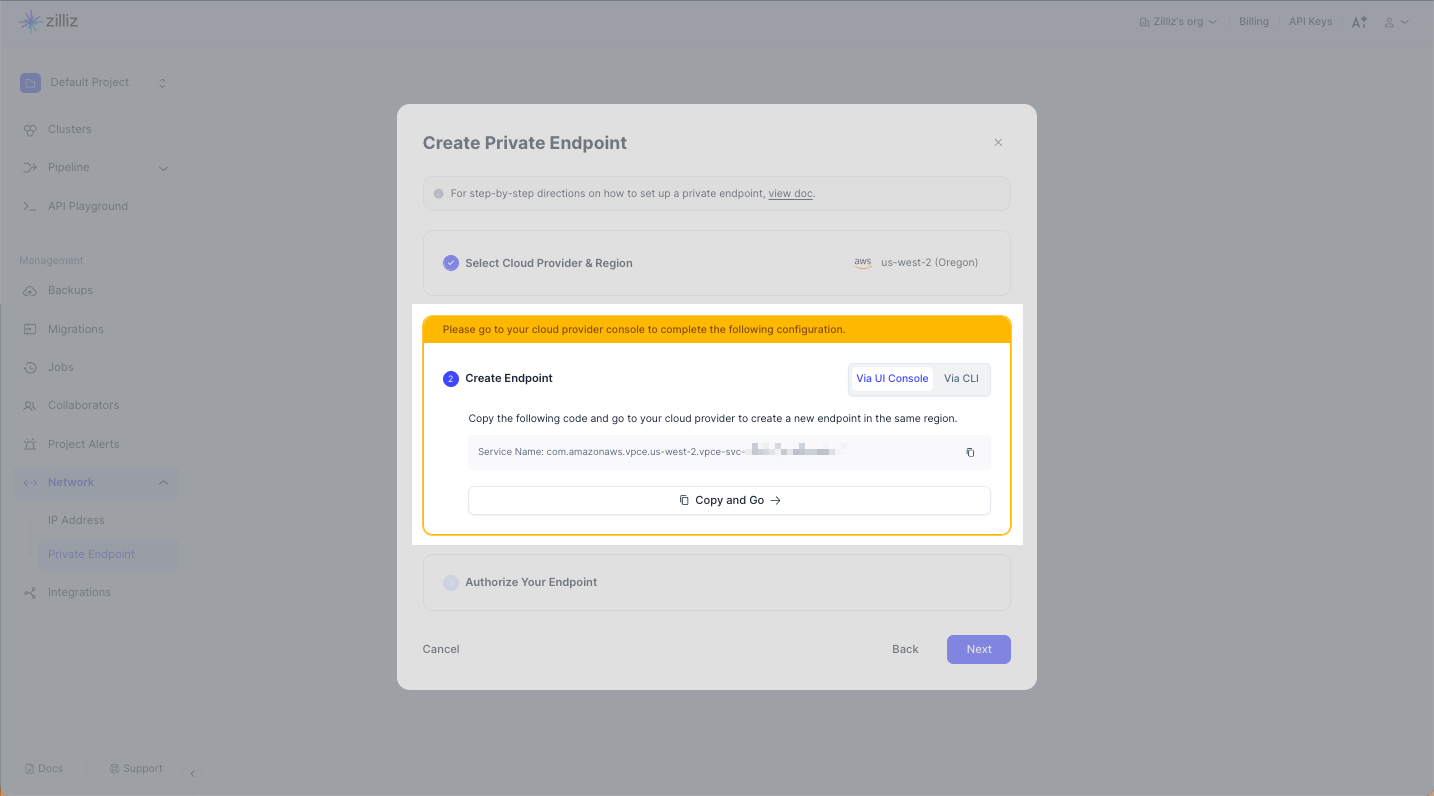 1
1Switch to the Via UI Console tab, and copy the Service Name.
2Navigate to the AWS console and select the region where your service runs in the upper-right corner. Then, click Endpoints in the left navigation. Click Create Endpoint.
📘NotesYou should always use the region where your service that needs access to your Zilliz Cloud cluster is located.
If your service runs in the same region as the one hosting your Zilliz Cloud cluster, use the region.
If your service runs in a different region than the one hosting your Zilliz Cloud cluster, use the region where your service runs.
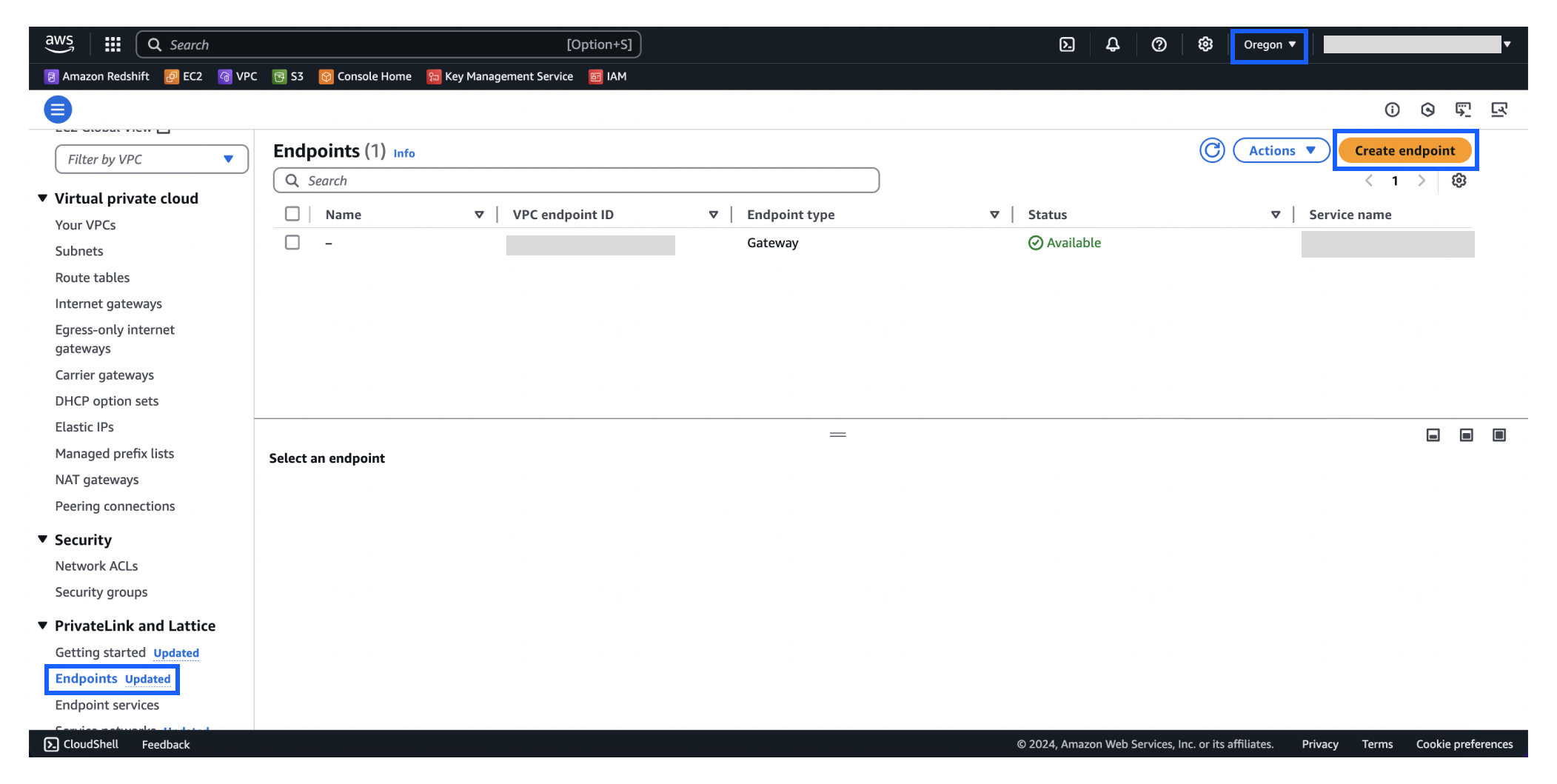 3
3On the Create Endpoint page, select Endpoint services that use NLBs and GWLBs as the endpoint Type.
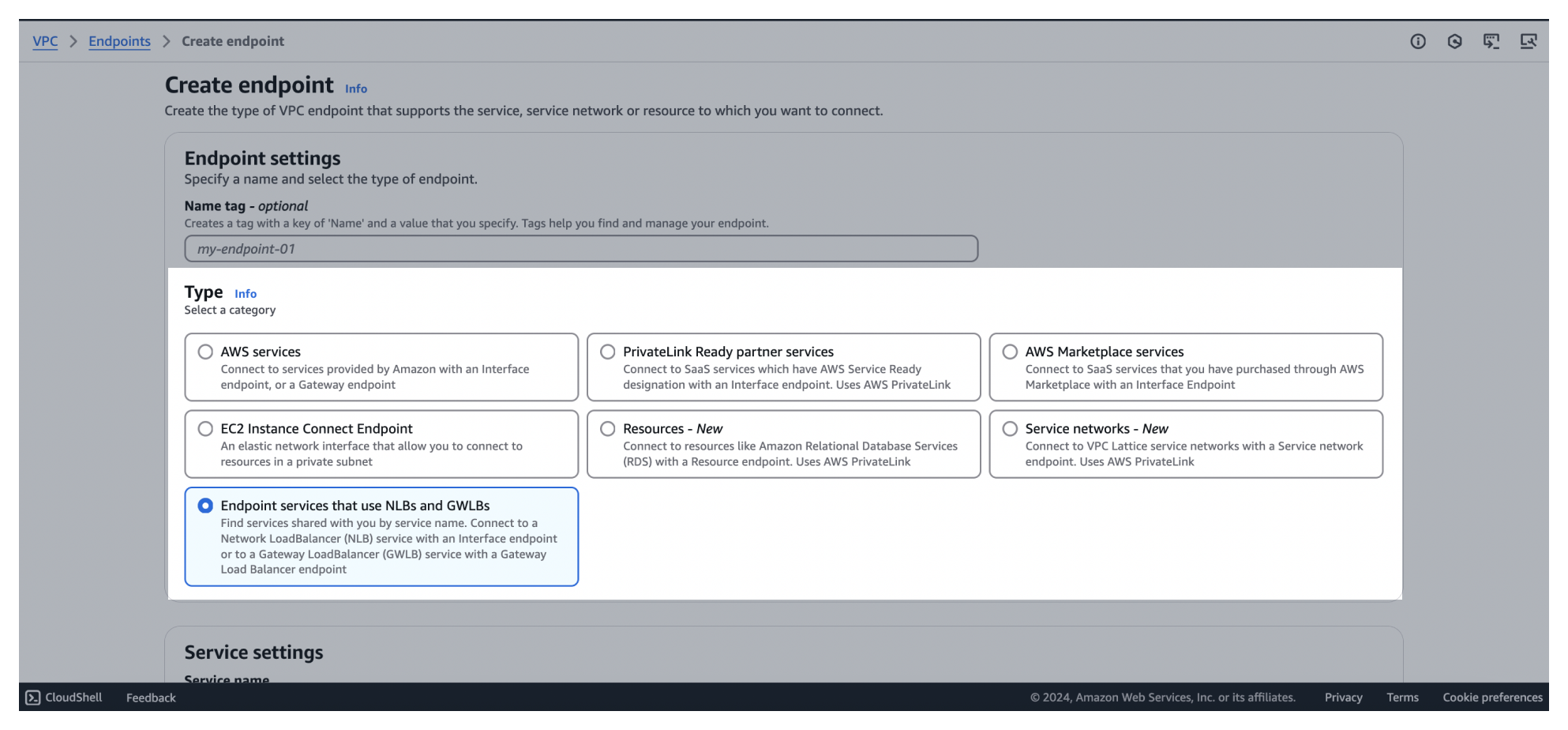 4
4Switch to the AWS console. In Service Settings, paste the Service Name you copied from the Zilliz Cloud web console into the Service Name field. Then click Verify service.
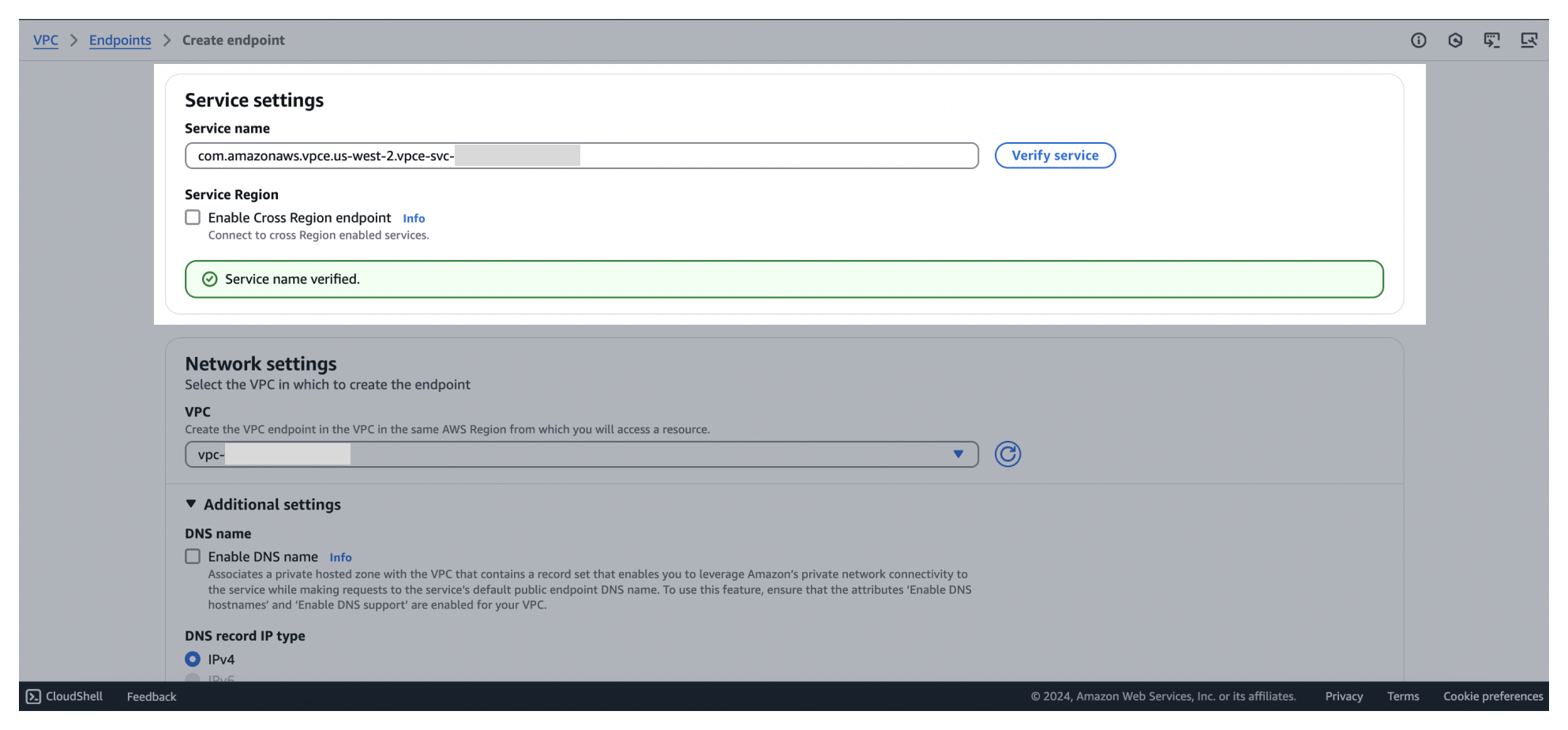 📘Notes
📘NotesIf your service operates in a different region than where your Zilliz Cloud cluster is hosted, ensure you select Enable Cross Region endpoint and choose the region where your Zilliz Cloud cluster runs. Then click Verify service.
In the following diagram, your Zilliz Cloud cluster is assumed to be running in Europe (Frankfurt), and your service is running in another region.
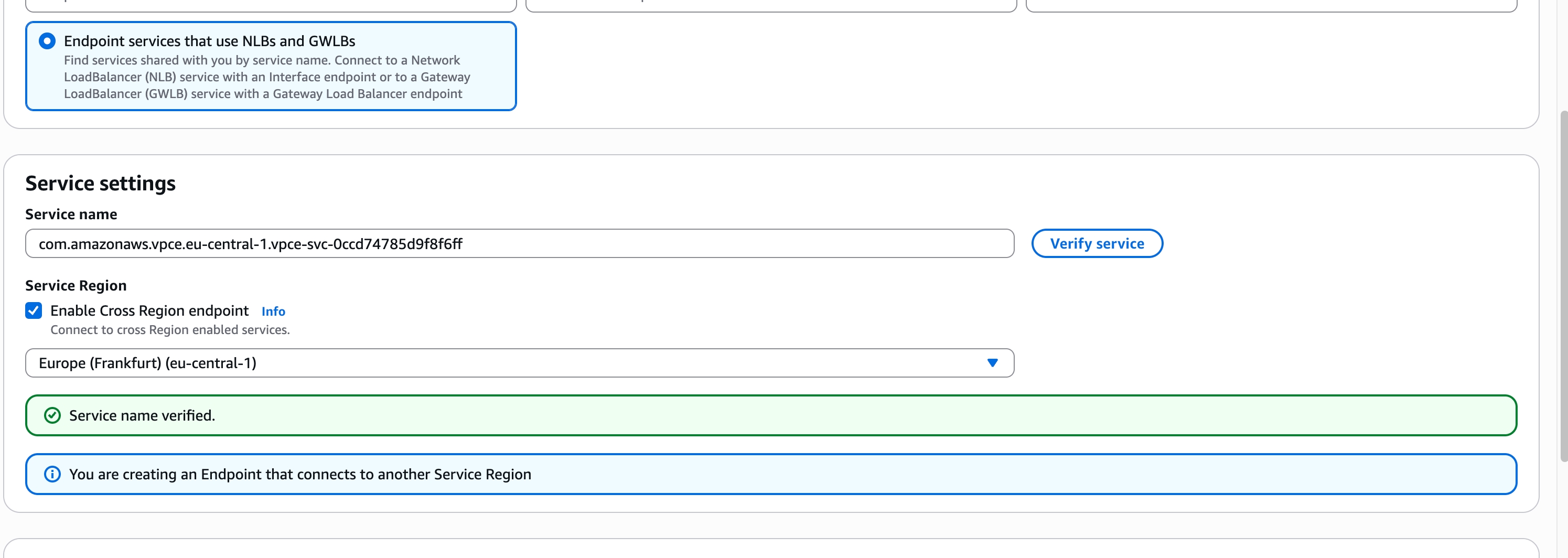 5
5When the service name is verified, complete network settings, subnet, security groups, and click Create.
6When the endpoint is successfully created, copy the Endpoint ID (starting with "vpce-").
-
Via CLI
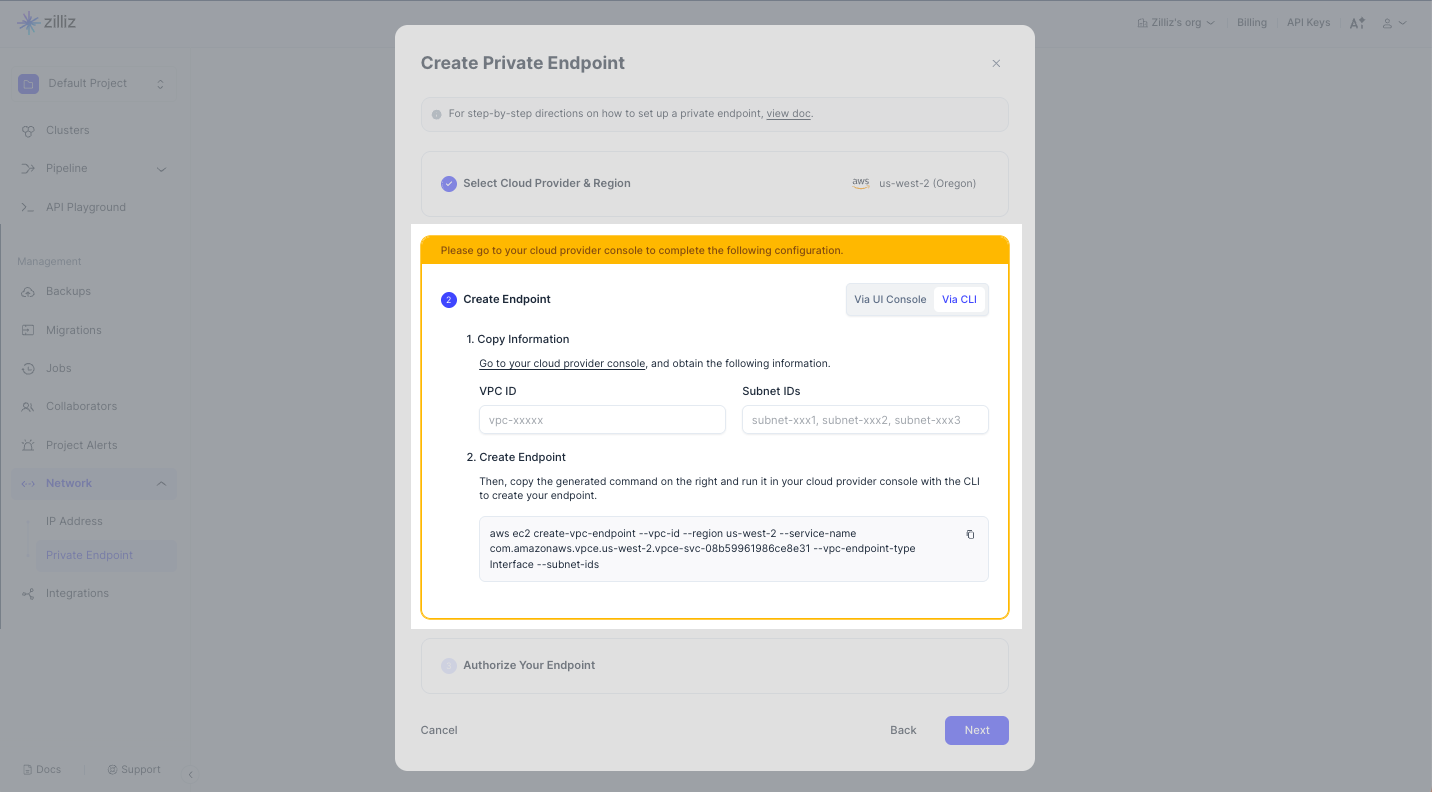 1
1Switch to the Via CLI tab.
2Enter the VPC ID.
To view your VPCs, navigate to the Amazon VPC console. In the navigation pane, choose Your VPCs. Find the VPC of your desire and copy its ID. Enter this ID in VPC ID on Zilliz Cloud.
To create a VPC, see Create a VPC.
3Enter the Subnet IDs.
Subnets are sub-divisions of your VPC. You need to have a subnet that resides in the same region as the private endpoint to be created. To view your subnets, navigate to the Amazon VPC console. Change the current region to the one specified for creating the private link. In the navigation pane, choose Subnets. Find the subnet of your desire and copy its ID. Enter this ID in Subnet IDs on Zilliz Cloud.
To create a subnet, see Create a Subnet in Your VPC.
4Click the copy icon in the code block and go to the AWS console.
In the top navigation, launch AWS CloudShell. Run the CLI command you just copied from Zilliz Cloud in the CloudShell.
The returned message is similar to the following:
{
"VpcEndpoint": {
# Copy this and fill it in "Your VPC Private Link ID"
"VpcEndpointId": "vpce-0ce90d01341533a5c",
"VpcEndpointType": "Interface",
...
"DnsEntries": [
{
# Copy this one and use it as "VPCE_DNS" in the next step.
"DnsName": "vpce-0ce90d01341533a5c-ngbqfdnj.vpce-svc-0b62964bfd0edfb74.us-west-2.vpce.amazonaws.com",
"HostedZoneId": "Z1YSA3EXCYUU9Z"
},
{
"DnsName": "vpce-0ce90d01341533a5c-ngbqfdnj-us-west-2a.vpce-svc-0b62964bfd0edfb74.us-west-2.vpce.amazonaws.com",
"HostedZoneId": "Z1YSA3EXCYUU9Z"
}
]
}In the returned message, copy the VpcEndpointId (starting with "vpce-") of the created VPC endpoint.
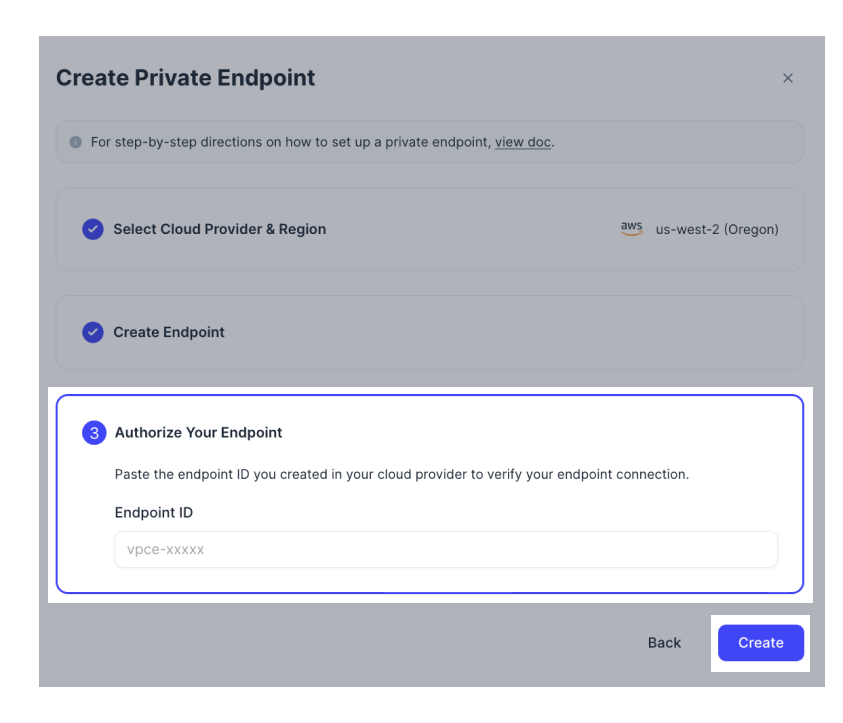
Step 3: Authorize your endpoint
Paste the endpoint ID you obtained from the AWS console into the Endpoint ID box on Zilliz Cloud. Click Create.
Obtain a private link
After verifying and accepting the VPC endpoint you have submitted, Zilliz Cloud allocates a private link for this endpoint. This process takes about 5 minutes.
When the private link is ready, you can view it on the Private Link page on Zilliz Cloud.
Set up a DNS record
Before you can access your cluster via the private link allocated by Zilliz Cloud, it is necessary to create a CNAME record in your DNS zone to resolve the private link to the DNS name of your VPC endpoint.
-
Create a hosted zone using Amazon Route 53
Amazon Route 53 is a web-based DNS service. Create a hosted DNS zone so that you can add DNS records to it.
 1
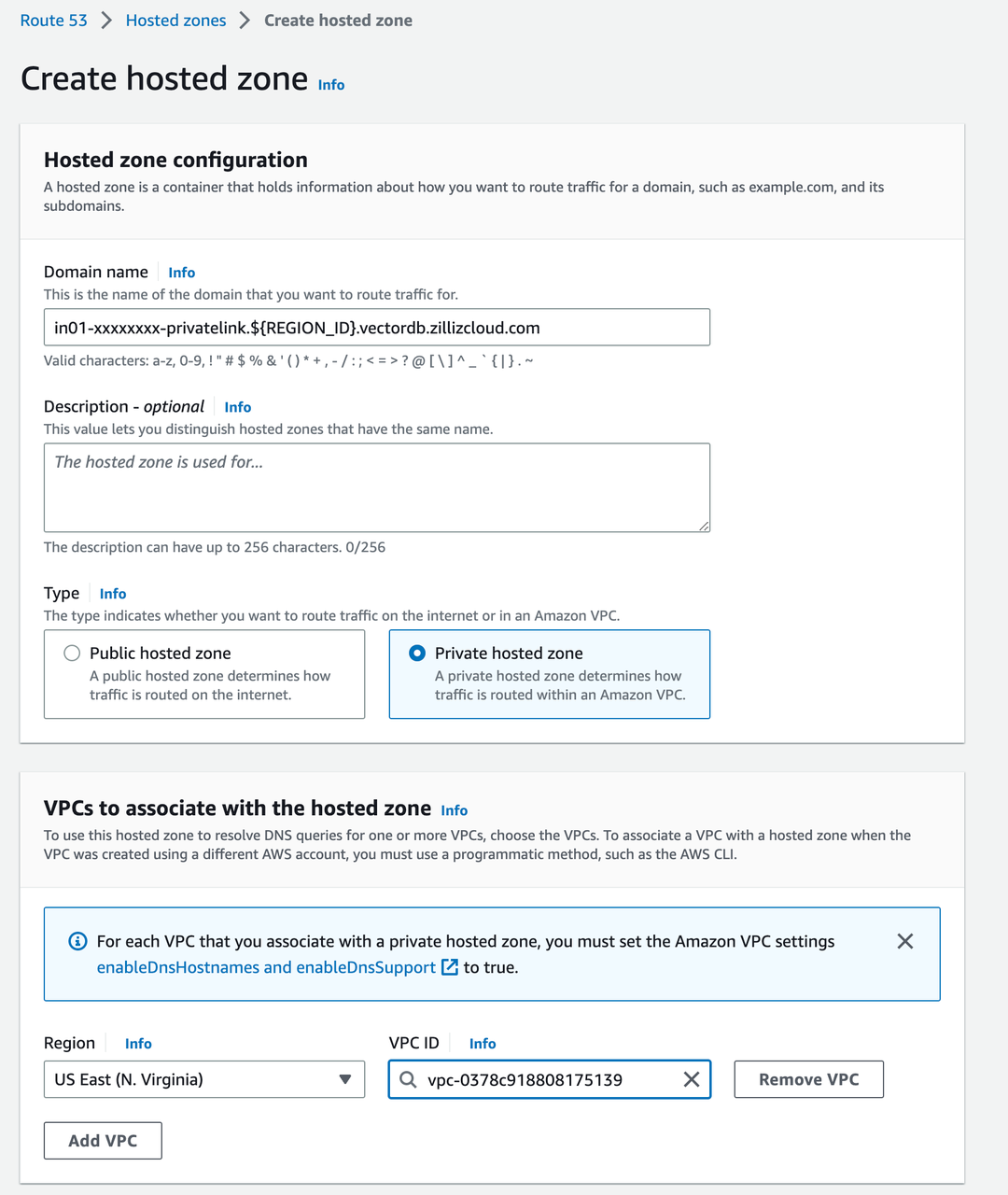
1Log into your AWS account and go to Hosted zones.
2Click Create hosted zone.
3In the Hosted zone configuration section, set the following parameters.
Parameter name
Parameter Description
Domain name
Private Link allocated by Zilliz Cloud for the target cluster.
Description
Description used to distinguish hosted zones.
Type
Select Private hosted zone.
4In the VPCs to associate with the hosted zone section, add your VPC ID to associate it with the hosted zone.
-
Create an alias record in the hosted zone
An alias record is a type of DNS record that maps an alias name to a true or canonical domain name. Create an alias record to map the private link allocated by Zilliz Cloud to the DNS name of your VPC endpoint. Then, you can use the private link to access your cluster privately.
 1
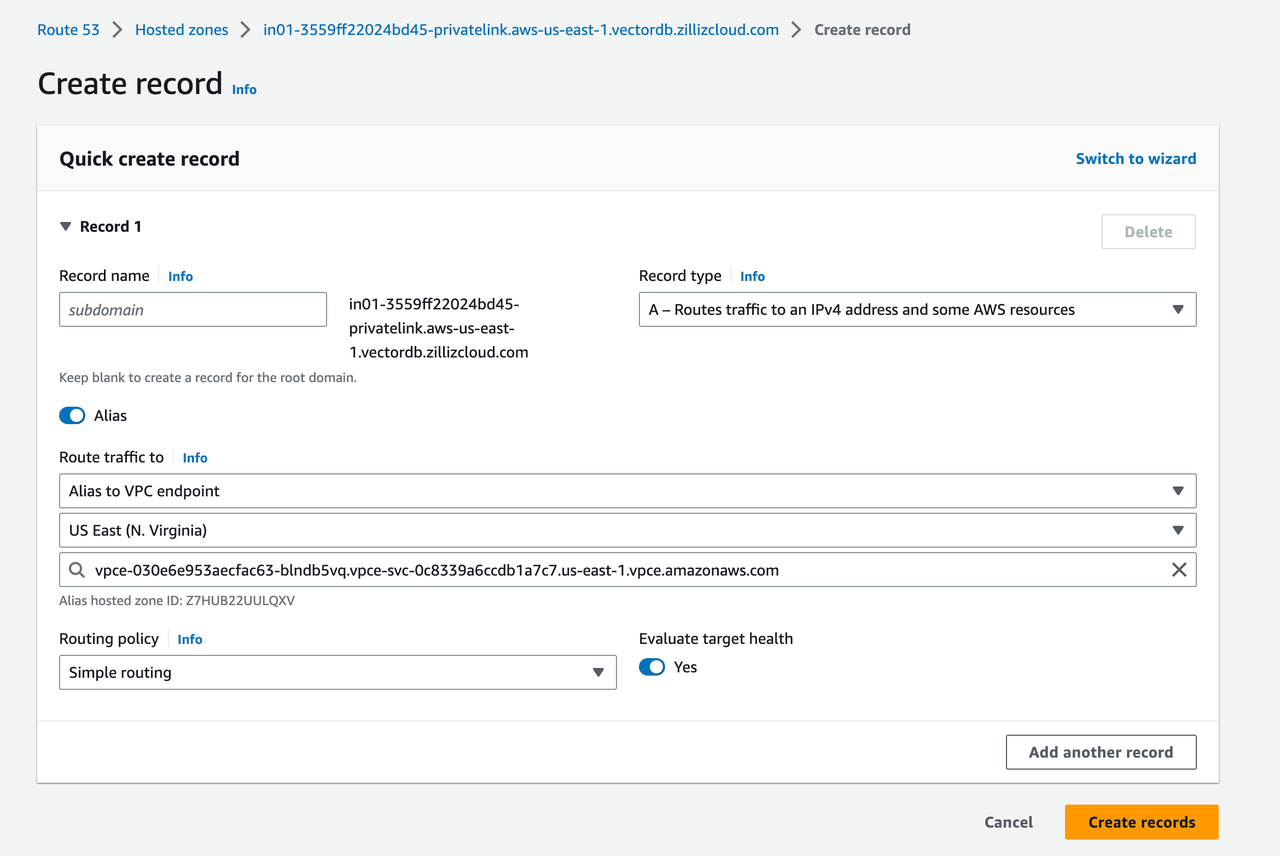
1In the created hosted zone, click Create record.
2On the Create record page, switch on Alias, and select Route traffic to as follows:
-
Select Alias to VPC endpoint in the first drop-down list.
-
Select the cloud region in the second drop-down list.
-
Enter the name of the endpoint that has been created above.
3Click Create records.
-
Manage internet access to your clusters
After configuring your private endpoint, you can choose to disable the cluster public endpoints to restrict internet access to your project. Once you have disabled the public endpoint, users can only connect to the cluster using the private link.
To disable public endpoints:
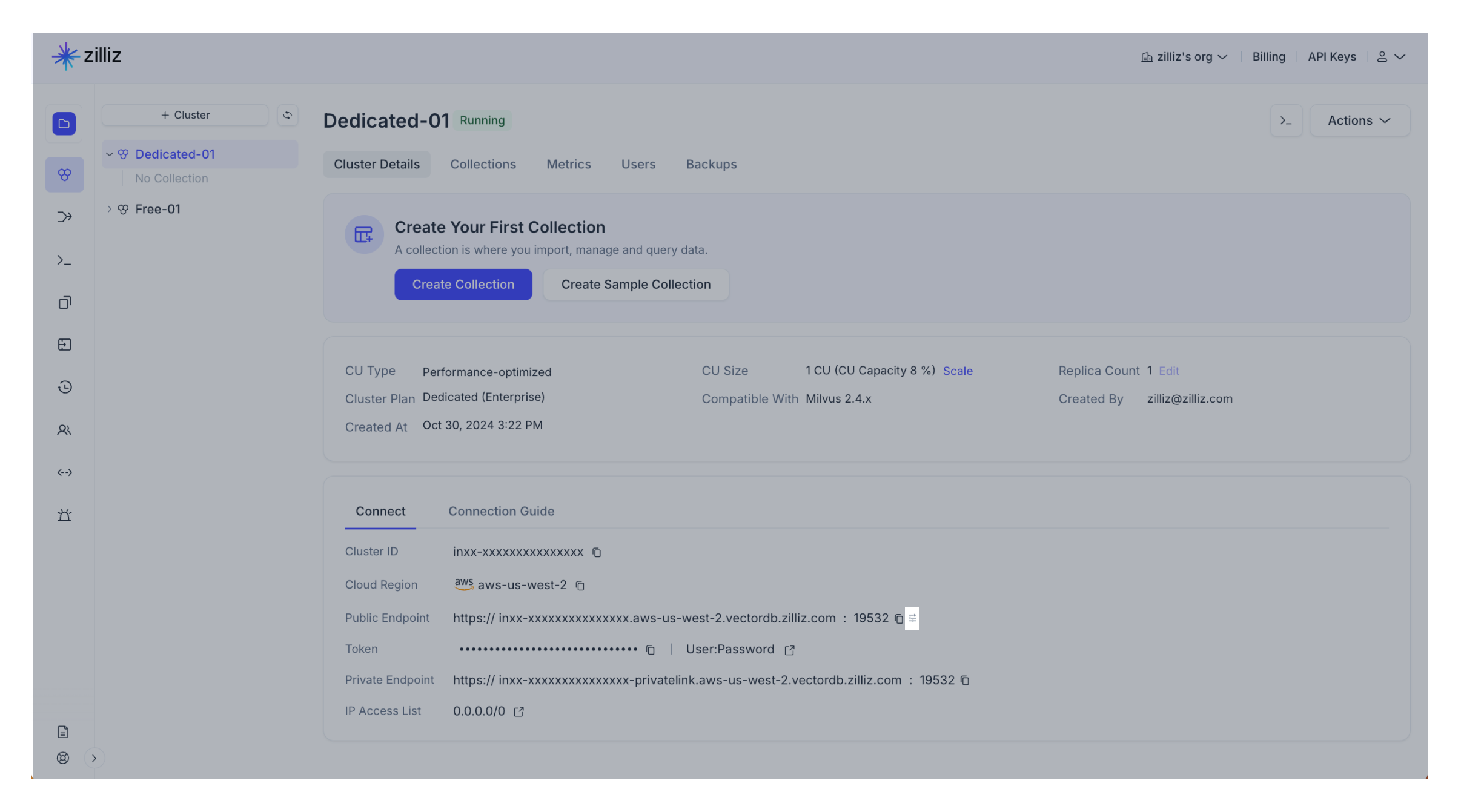
Go to the Cluster Details page of your target cluster.
Navigate to the Connect section.
Click on the configurations icon next to the cluster public endpoint.
Read the information and click Disable in the Disable Public Endpoint dialog box.
Private endpoints only impact data plane access. Control plane can still be accessed over the public internet.
After you re-enable the public endpoint, you may need to wait until the local DNS cache to expire before you can access the public endpoint.
FAQ
Why does it always report a timeout when connecting to the private link on AWS?
A timeout usually occurs for the following reasons:
-
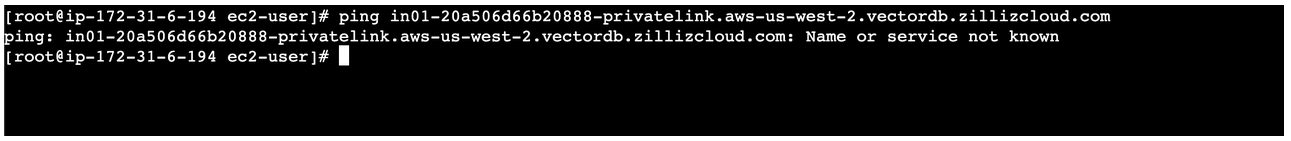
No private DNS records exist.
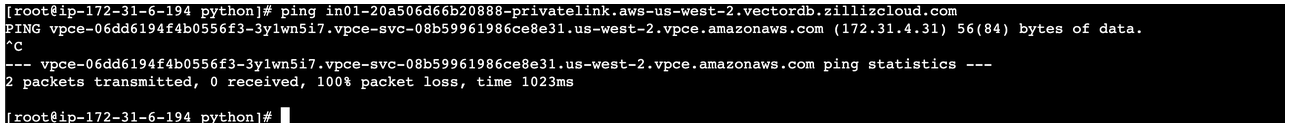
If a DNS record exists, you can ping the private link as follows:
 📘Notes
📘NotesIf the IP address of the VPC endpoint has been resolved correctly in the output of the ping request, the DNS record works.
If you see the following, you need to set up the DNS record.
-
No or invalid security group rules exist.
You need to properly set the security group rules for the traffic from your EC2 instance to your VPC endpoint in the AWS console. A proper security group within your VPC should allow inbound access from your EC2 instances on the port suffixed to your private link.
You can use a
curlcommand to test the connectivity of the private link. In a normal case, it returns a 400 response.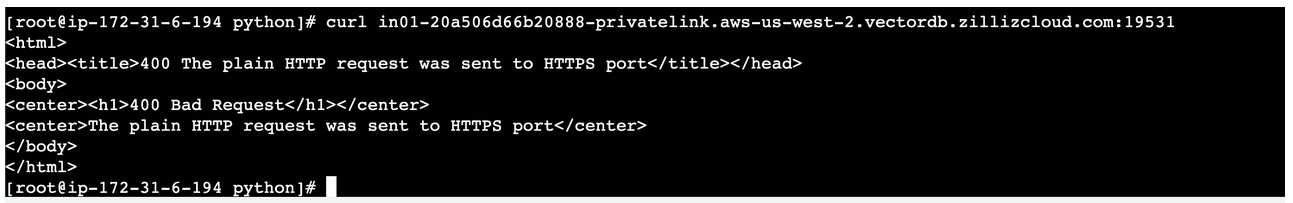
If the
curlcommand hangs without any response as in the following screenshot, you need to set up proper security group rules by referring to step 9 in Create a VPC endpoint.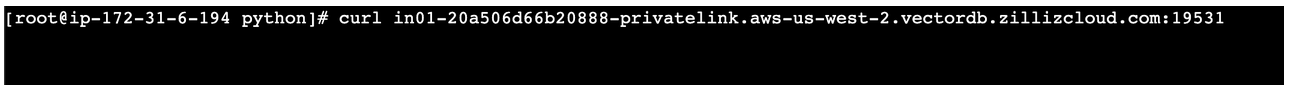 📘Notes
📘NotesTwo security groups must be configured: one for the EC2 instance, which must allow traffic on the port associated with your private link, and another for the VPC endpoint, which must permit traffic from the IP address of the EC2 instance and target the specified port number.
Can I create a private endpoint for an existing cluster?
Yes. When you create a private endpoint, it will take effect on all existing and future Dedicated (Enterprise) clusters that reside in the same region and project. All you need to do is to add different DNS records for different clusters.